There is almost certainly no smartphone privacy app that you can install on your phone to block monitoring and spying by the “government,” meaning the Total Information Awareness system constructed by the NSA and other security/intelligence agencies in the United States. There are almost certainly low level hardware or firmware backdoors in all popular smartphones such as Apple’s iPhone and the many Android phones that enable the “government” to access the phones at will. These backdoors operate at a low level below any installed app.

In the case of the iPhone the backdoors are probably in the Apple multitouch firmware that customers use to enter their password and interact with the iPhone; it is a little known but not secret fact that the US Central Intelligence Agency (CIA) funded the development of this multitouch technology at Fingerworks which was acquired by Apple both for the software and the Fingerworks development team.
The US Central Intelligence Agency (CIA) Funded the Core Multitouch Technology in the Apple iPhone: qz.com/1669346/mariana-mazzucatos-plan-to-use-governments-to-save-capitalism-from-itself
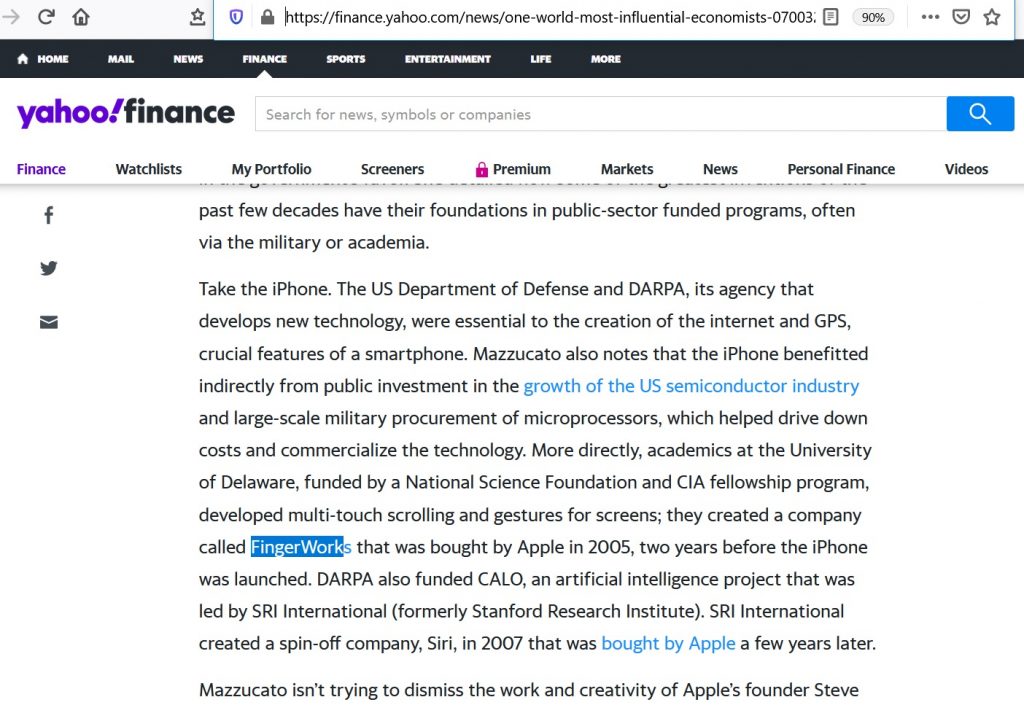
Also at Yahoo Finance: https://finance.yahoo.com/news/one-world-most-influential-economists-070032353.html
“More directly, academics at the University of Delaware, funded by a National Science Foundation and CIA fellowship program, developed multi-touch scrolling and gestures for screens; they created a company called FingerWorks that was bought by Apple in 2005, two years before the iPhone was launched.”
The American Civil Liberties Union (ACLU) has sued the FBI about their mysterious iPhone breaking capabilities.
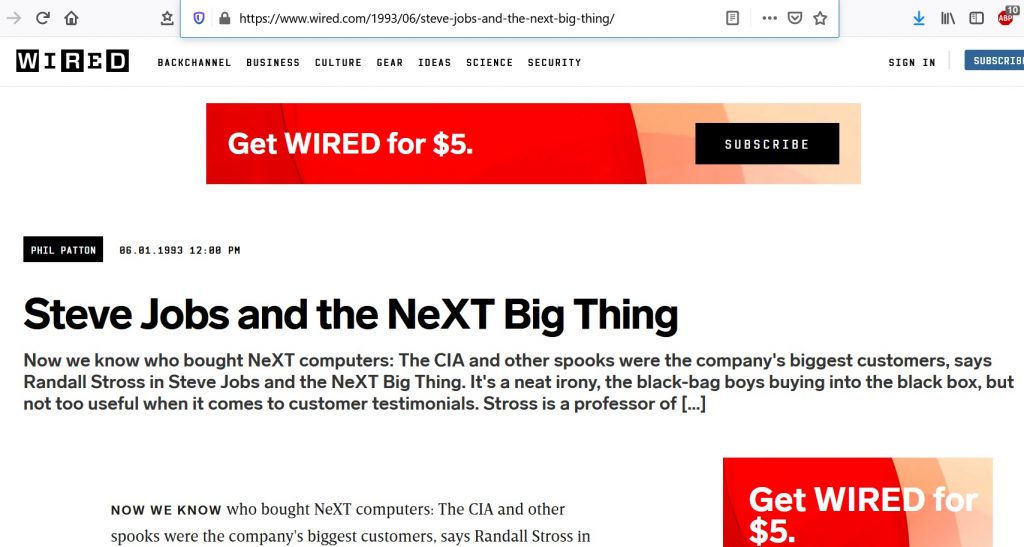
It is also a little known fact that the US CIA was an early customer of Steve Jobs Next Computer company before it was acquired by Apple. (see the original hardcover edition of Steve Jobs and the NeXT Big Thing by Randall Stross).
Low Level Smartphone Backdoors are Very Risky
These low level smartphone backdoors are very risky. With a large fraction of the human race using smartphones, they are tempting for abuse and almost certainly are being badly abused by the small cadre of intelligence officials with access to the system. The most likely abuse is mass/global scale blackmail and psychological manipulation for the acquisition of money and power. As the case of former New York governor Elliot Spitzer illustrates, many powerful people are remarkably careless with their electronic communications and would be subject to manipulation or blackmail by anyone with access to this system.
These backdoors are a high value target for the intelligence services of various nations such as Russia and China as well as organized criminal gangs, terrorists, and other groups. They are vulnerable to technological surprise by other as yet unknown actors who may develop the technology to take over the system or somehow already have the capability.
What Can You Do to Protect Your Privacy?
The reality is there is no app you can install to protect yourself and continue to use a smartphone — or many other devices — in the modern world of nearly ubiquitous high speed wireless networks. The practical options at present are either simply to stop using smartphones entirely or keep them in a sealed radio proof case, a “Faraday bag,” except for emergencies and special situations.
Such cases are currently available for purchase at Amazon and other sources. One can also use hermetically sealed metal food containers that are still widely available. Some games and other products are also marketed in such containers. It is possible to make secure cases for smartphones using metal foil (aluminum foil), painters tape or other tapes, and a ruler and pair of scissors — all common inexpensive household items.



More detailed information on these options can be found here:
and here:
Alternate Video Links: BitChute NewTube Brighteon
How to Stop Your Phone from Spying on You? Demonstrates methods to isolate your phone from cellular and other radio networks while keeping the phone easily accessible for emergencies or other special cases.
Products Demonstrated:
Secure Case (Faraday Bag): https://www.amazon.com/gp/product/B01HETGX00/
ZOMAKE Lightweight Backpack: https://www.amazon.com/ZOMAKE-Lightweight-Packable-Backpack-Resistant/dp/B074SG7ZTK
We do not receive any compensation for using or demonstrating these products.
(C) 2020 by John F. McGowan, Ph.D.
About Me
John F. McGowan, Ph.D. solves problems using mathematics and mathematical software, including developing gesture recognition for touch devices, video compression and speech recognition technologies. He has extensive experience developing software in C, C++, MATLAB, Python, Visual Basic and many other programming languages. He has been a Visiting Scholar at HP Labs developing computer vision algorithms and software for mobile devices. He has worked as a contractor at NASA Ames Research Center involved in the research and development of image and video processing algorithms and technology. He has published articles on the origin and evolution of life, the exploration of Mars (anticipating the discovery of methane on Mars), and cheap access to space. He has a Ph.D. in physics from the University of Illinois at Urbana-Champaign and a B.S. in physics from the California Institute of Technology (Caltech).

